The Domain Name System Security Extensions (DNSSEC) is a pivotal advancement in DNS, introducing cryptographic authentication to verify the authenticity of DNS records. By addressing critical vulnerabilities in the traditional DNS infrastructure, DNSSEC safeguards against DNS-based attacks like spoofing and cache poisoning.
The Foundation of DNSSEC
DNSSEC enhances the traditional DNS by integrating digital signatures into DNS records. These signatures create a verifiable chain of trust that extends from the root zone to individual domain names, ensuring both data authenticity and integrity.
How Does DNSSEC Work?
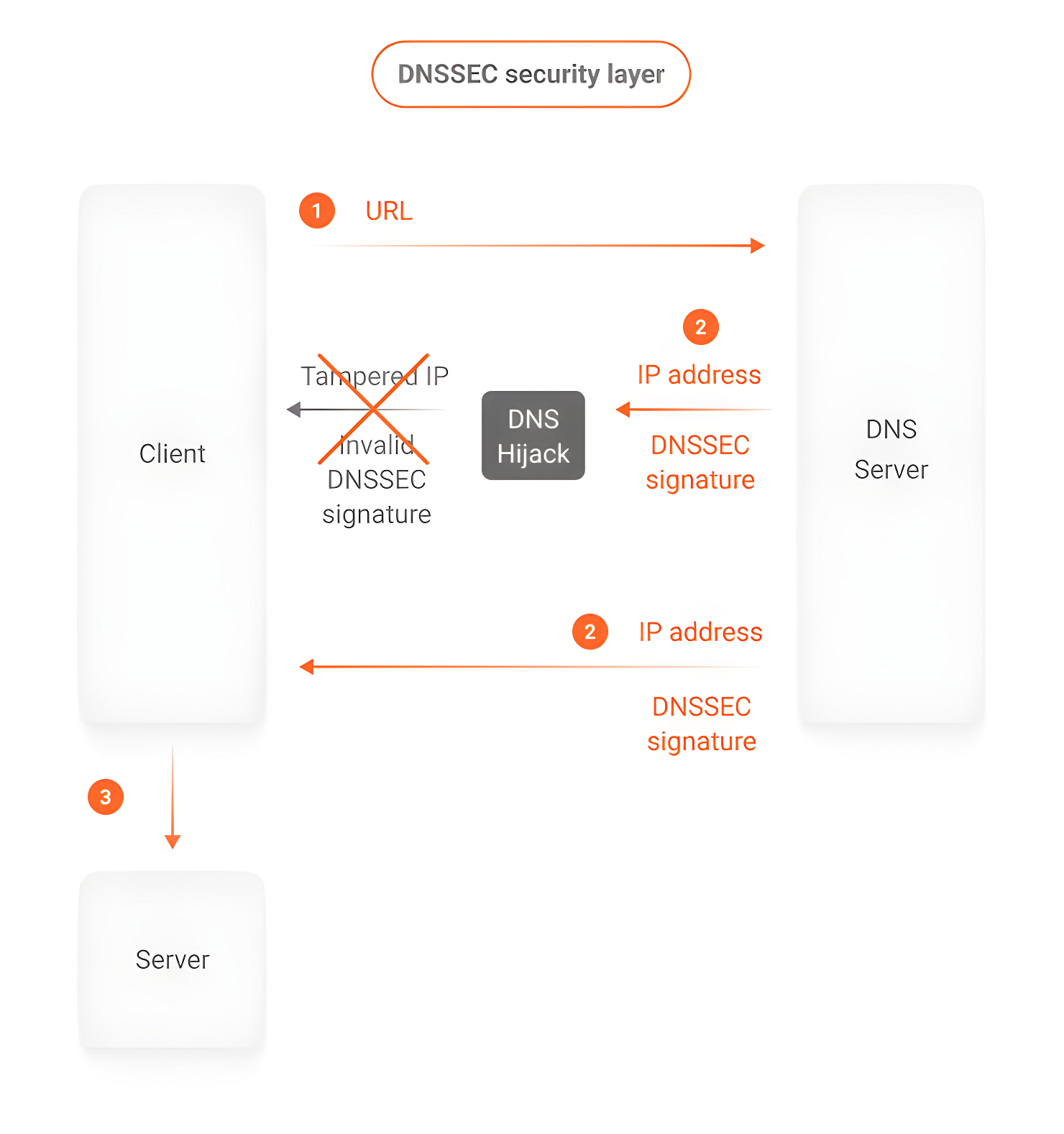
In short, DNSSEC solves one of the biggest issues with the original DNS specification: there is no way to authenticate the responses from a server. This opens the door for attacks such as DNS Spoofing, where an attacker can impersonate a server and deliver a response with false data about a domain, such as a different IP address, redirecting traffic to servers under their control.
DNSSEC solves this by signing responses from compatible servers with a cryptographic key. By comparing signatures, it’s possible to authenticate a response, making it difficult for an attacker to manipulate information.
It’s worth mentioning that DNSSEC doesn’t implement data encryption: data continues to flow in clear text. An analogy is a document with a notarized signature: the signature alone guarantees the document’s authenticity, but does nothing to protect its content.
Key Resource Record Types in DNSSEC
DNSSEC relies on three essential resource record types to enable its cryptographic security features:
- DNSKEY Records: Store public keys for verifying digital signatures. These keys act as the foundation for DNSSEC validation.
- RRSIG Records: Contain the digital signatures of DNS zone data, ensuring their authenticity.
- DS Records: Link a child zone’s DNSKEY records to the parent zone, forming the hierarchical chain of trust.
Cryptographic Authentication in DNSSEC
The Role of Digital Signatures
Digital signatures are the backbone of DNSSEC. Using public-private key cryptography:
- Zone Owners: Sign DNS data with private keys, creating digital signatures stored in RRSIG records.
- Resolvers: Use the public key (from DNSKEY records) to verify the signatures and authenticate the data.
Key Types in DNSSEC
DNSSEC employs two types of cryptographic keys, each with specific roles:
-
Zone Signing Keys (ZSK):
- Sign DNS records within the zone.
- Ensure all zone data is verifiable as authentic.
-
Key Signing Keys (KSK):
- Sign the ZSK.
- Establish the chain of trust to the DNS root zone.
Core Components of DNSSEC
The core components of DNSSEC—Private Key, Public Key, and RRSIG Records—work together to ensure the authenticity and integrity of DNS data through cryptographic signing and verification.
| Component | Function | Purpose |
|---|---|---|
| Private Key | Signs DNS records | Creates digital signatures to ensure data authenticity. |
| Public Key | Verifies signatures | Validates the authenticity of DNS records. |
| RRSIG Records | Hold digital signatures | Prove the authenticity and integrity of DNS records. |
The Chain of Trust
The chain of trust begins at the DNS root zone and flows hierarchically through top-level domains to individual domain names. At each level:
- The parent zone signs the child zone’s DS records, which link to the child’s DNSKEY records.
- This creates a continuous validation path ensuring all DNS data is trustworthy.
DNSSEC in Action
The validation process ensures DNS data integrity by verifying digital signatures, linking keys in a trust chain, and authenticating responses to protect against spoofing and tampering.
Validation Process
| Step | Action | Result |
|---|---|---|
| Query Receipt | Resolver receives request | Initiates DNSSEC validation. |
| Signature Check | Verify RRSIG records | Confirms data authenticity. |
| Key Verification | Validate DNSKEY | Establishes a trust chain. |
Benefits of DNSSEC
Enhanced Security
- Protection Against DNS Spoofing: Prevents malicious redirection by verifying DNS responses.
- Resistance to Tampering: Maintains data integrity during transit.
- Increased Trust: Builds user confidence in the DNS infrastructure, reducing phishing risks.
Defense Against Common Attacks
DNSSEC safeguards against threats like cache poisoning, DNS spoofing, and man-in-the-middle attacks by employing cryptographic authentication and data integrity verification.
| Threat | Protection Method | Outcome |
|---|---|---|
| Cache Poisoning | Signature validation | Prevents false records. |
| DNS Spoofing | Origin authentication | Ensures data authenticity. |
| Man-in-the-Middle | Cryptographic verification | Maintains data integrity. |
Challenges and Mitigations
While DNSSEC offers robust security, its implementation can pose challenges:
- Complexity: Requires expertise in setup and maintenance.
- Performance Impact: Cryptographic operations may introduce latency.
- Key Management: Demands secure policies for key generation, rotation, and revocation.
Mitigation: Edge Platforms simplify DNSSEC by offloading validation processes to the edge, improving performance without sacrificing security.
Best Practices for DNSSEC Deployment
Successful DNSSEC deployment and maintenance requires adherence to the following best practices:
-
Ensure Proper Configuration: Correctly configuring DNSSEC records (DNSKEY, RRSIG, and DS) on the authoritative DNS servers is crucial for establishing a valid chain of trust.
-
Implement Robust Key Management: Develop and follow a comprehensive key management policy, including regular key rollovers and secure key storage procedures.
-
Coordinate with Ecosystem Partners: Collaborate closely with domain registrars, DNS providers, and other relevant parties to ensure a seamless DNSSEC deployment across the entire DNS infrastructure.
-
Perform Regular Monitoring and Troubleshooting: Continuously monitor DNSSEC validation status and be prepared to quickly address any issues that may arise, such as key expiration or validation failures.
-
Educate End-Users: Provide clear guidance and resources to help end-users (or their IT teams) understand the importance of DNSSEC and how to configure their systems to utilize its security features.
By following these best practices, organizations can ensure that their DNSSEC deployment is secure, efficient, and resilient, providing robust protection for their DNS infrastructure.
Conclusion
DNSSEC plays a critical role in modern DNS infrastructure by ensuring the authenticity and integrity of DNS records through cryptographic measures. Its hierarchical chain of trust protects against DNS-based attacks, fostering a more secure and trustworthy internet. As DNSSEC evolves, its integration with new technologies like edge computing and AI will continue to provide scalable and robust solutions for DNS security.