Simplify your journey and protect your business with Security Automation
As cyber threats grow more sophisticated, security automation has become essential for organizations to streamline repetitive and time-consuming tasks, manage their security posture, and scale their operations effectively.
In this context, autonomous systems operate with minimal or no human intervention, using artificial intelligence (AI) and security automation to detect, prevent, and respond to threats. Implementing these systems offers the following benefits:
- Real-time threat detection through advanced AI algorithms.
- Continuous self-improvement and learning by AI and automated systems.
- Improved scalability to efficiently handle large volumes of data and events.
- Automated responses based on predefined behaviors and rules to mitigate threats.
- Predictive analytics to anticipate and address potential security risks.
- Enhanced operational efficiency with minimal intervention, reducing human error.
- Protection against increasingly sophisticated threats like phishing, malware, prompt injection, adversarial manipulation, and data leaks in modern applications.
Security Automation Architecture Diagram
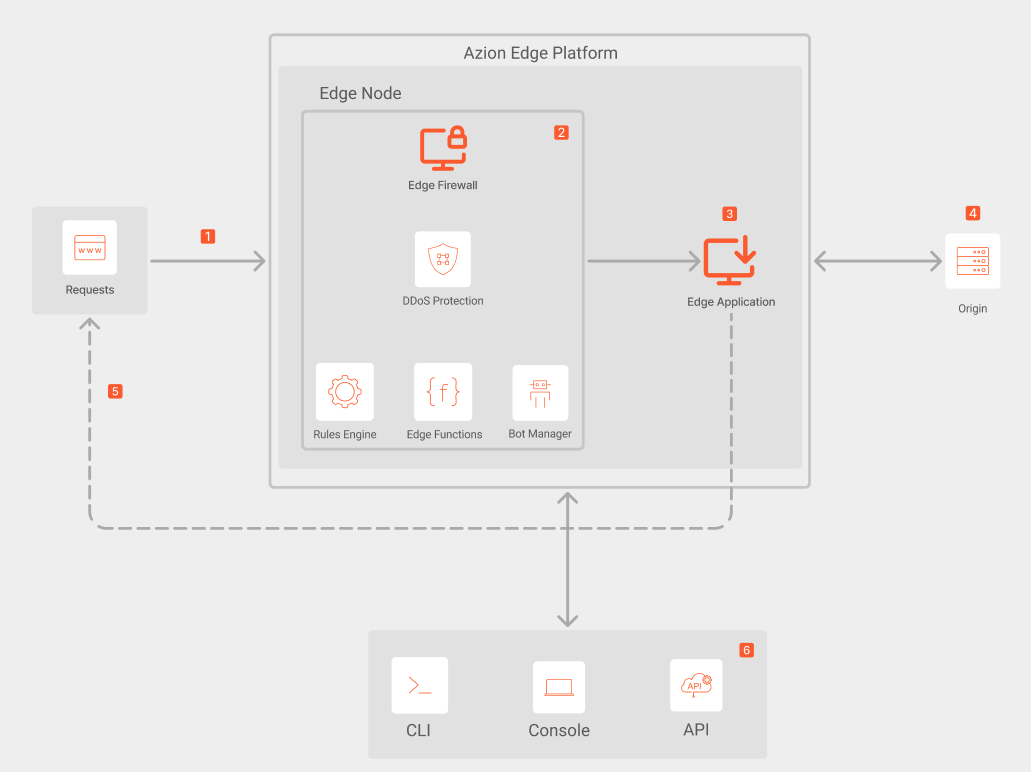
Security Automation Dataflow
- A request reaches Azion Edge Platform and is redirected to the healthier edge node.
- In the edge node, Edge Firewall processes the request and executes the security configurations:
- DDoS Protection checks for potential DDoS or DoS attacks, blocking or allowing the request accordingly. It’s automatically enabled in all accounts.
- Edge Firewall Rules Engine identifies if there are rules from WAF and Network Layer Protection, and executes the corresponding behaviors.
- Any configured and instantiated edge function is executed. Read more on how to automate security with Azion Edge Functions.
- Bot Manager also analyzes the request using machine learning, intent-based behavioral analysis, and advanced algorithms.
- If the request doesn’t match an Edge Firewall rule and isn’t blocked, the request continues the flow to Edge Application.
- Edge Application Rules Engine identifies if there are rules related to caching, image optimization, cookies, and redirects, among others.
- The request only reaches the origin in case the edge node doesn’t contain the required response, after passing all the implemented security policies.
- The system responds to the request accordingly.
- Customers can monitor traffic and refine configurations, rules, and automation through Azion interfaces: Console, API, or CLI.
Components
- Azion interfaces: Console, API, or CLI.
- Edge Firewall: provides main settings to set up your instance, enabling you to associate it with domains and activate modules to protect users, applications, and networks.
- DDoS Protection detects and mitigates DDoS and DoS attacks.
- Edge Firewall Rules Engine allows you to define the conditions (Criteria) and actions (Behaviors) for your rules. If the Criteria are met, the Behaviors will be executed.
- Edge Firewall Edge Functions are JavaScript functions that run at the edge of the network, close to users, and help secure your applications by applying the logic your business requires.
- Bot Manager identifies and classifies the request according to the intent-based behavioral analysis. This add-on is Azion’s comprehensive solution for bot management. A lite version integration is also available in the Marketplace.
Implementation
- Create an edge application.
- Configure an edge firewall.
- Define all your rules and configurations:
- Rules Engine rules, using criteria and behaviors to define how the request is handled. It includes rules related to network lists, WAF Rules, Custom Allowed Rules, rate limits, custom responses, blocking and dropping requests, and run functions.
- Edge Functions, creating your own code or using Marketplace Edge Firewall integrations.
- Enable Bot Manager:
- Contact the Sales team for more details about the Bot Manager subscription.
- Configure Bot Manager Lite if you’ve decided to use this version.
When saved, configurations are replicated across all edge nodes in the network. Whenever a request reaches Azion’s platform, the rules and configurations are executed, and the system processes the request accordingly. You can use Observe products to monitor and track traffic.
Related docs
- Implement a security perimeter around your API Gateway
- Protect your edge applications with a Bot Management solution
- Enhance cybersecurity with Azion’s advanced WAAP solution
- Secure an application
- Secure an infrastructure
- Secure DNS
Contributors