Reinforce online fraud prevention to protect digital business trust
As sensitive data flows across networks, online fraud prevention has become a cornerstone of any digital business’s success, especially e-commerce and financial services. Cyber threats continue to evolve, increasing both the volume and sophistication of attacks. These include account takeover attempts and automated and manual fraud schemes, such as credential stuffing, phishing attacks, card testing, synthetic identity fraud, and payment fraud.
To stay ahead, these businesses must adopt a proactive, multi-layered security strategy to protect their services, minimize friction, and build lasting user trust. A comprehensive security strategy includes a trusted technology partner that provides an integrated edge platform with the products and services you need to do so.
This includes network protection with zero-trust architecture, firewalls, bot management, and device detection for secure authentication. A Web Application Firewall (WAF) safeguards applications, while encryption and access controls protect sensitive data. Flexible integrations ensure that security measures adapt to your business needs.
This approach performs fraud detection directly at the edge before reaching your applications and origins. Additionally, continuous observability ensures that potential threats are identified and mitigated early, reducing the impact on your brand reputation and user experience and minimizing friction across all touchpoints.
Online Fraud Prevention Architecture Diagram
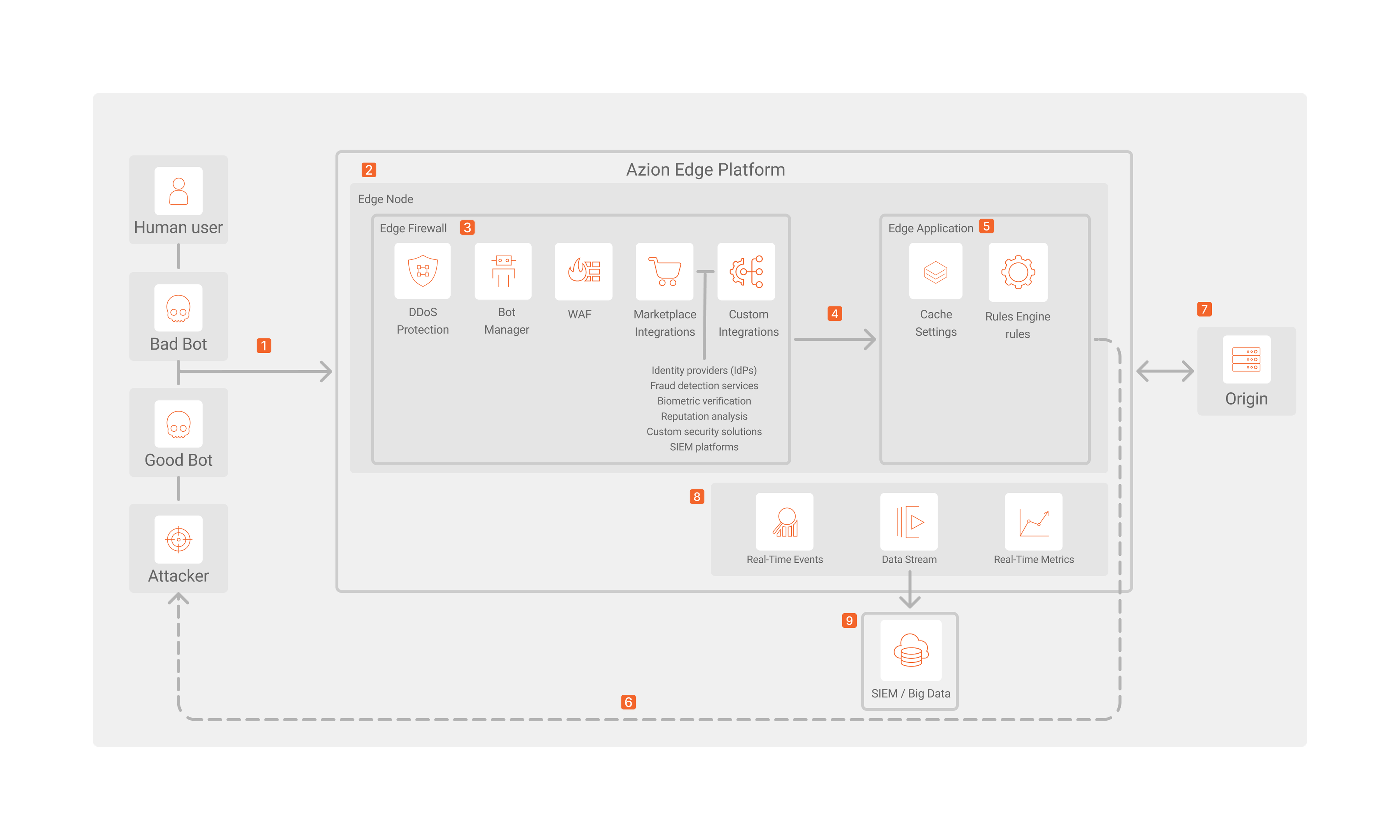
Online Fraud Prevention Dataflow
- A request reaches Azion Edge Platform.
- The platform has its own security mechanisms, including real-time monitoring and threat detection, encryption, access controls, protocols, and distributed firewalls. It also adheres to compliance requirements (PCI, SOC, LGPD/GPDR) and has a Security Response Team (SRT) that is constantly monitoring it.
- The platform sends the request to the healthiest edge node.
- After reaching the node, the request is analyzed by Edge Firewall:
- DDoS Protection checks for potential DDoS or DoS attacks, blocking or allowing the request accordingly. It’s automatically enabled in all accounts.
- Bot Manager assigns a score and classifies the request; then, executes the predefined preventive action:
allow,deny,drop,redirect,custom_html,random_delay, andhold_connection. - WAF Rules are applied and executed.
- The Rules Engine executes security rules based on the criteria and behaviors configured.
- Azion Marketplace Integrations for security are executed to complete the analysis and verification.
- Identity providers (IdPs).
- Fraud detection services.
- Biometric verification.
- Reputation analysis.
- Based on the firewall, account management, and integrations’ configurations, the system denies any unauthorized request. Otherwise, the request continues the flow to Edge Application.
- Edge Application executes all the configurations, according to the request:
- Optimized caching rules and advanced cache key settings to improve content delivery and efficiency.
- Device groups with targeted configurations based on device types for better control and security.
- Intelligent traffic distribution to improve availability, reliability, and performance through load balancing.
- Requests, response, and other Rules Engine rules.
- Edge Application resolves the request and sends an adequate response.
- The request only reaches the origin if the edge node doesn’t contain the necessary response, after passing through all the implemented security policies.
- Customers can use observability tools to monitor and act proactively against any threat:
- Real-Time Events enables access to detailed logs for real-time insights and auditing.
- Real-Time Metrics offers real-time visibility into performance and security trends through detailed graphics.
- Data Stream helps you send data to SIEM or Big Data tools for advanced analysis and threat detection.
- Customers also can seamlessly implement custom integrations with Azion to reinforce security, such as IdP, SSO, SIEM and Big Data platforms, and more.
Components
- Edge Network: a highly distributed architecture that includes strategically located edge nodes.
- Edge Application: allows you to build applications that run in Azion Edge Network.
- Application Accelerator: used to customize cache optimization rules, cache keys, and cookies based on established patterns.
- Edge Cache: global add-on to cache content at the edge.
- Edge Functions for Edge Application: allows you to create event-driven, serverless applications, at the edge of the network, closer to users.
- Rules Engine for Edge Application: allows you to configure scenarios where specific policies are enforced, providing granular control over delivery.
- Edge Firewall: provides main settings to set up your instance, enabling you to associate it with domains and activate modules to protect users, applications, and networks.
- DDoS Protection: detects and mitigates DDoS and DoS attacks.
- Web Application Firewall (WAF): allows you to configure protection against attacks and vulnerabilities.
- Bot Manager: Azion’s comprehensive solution for bot management.
- Edge Functions for Edge Firewall: build event-driven, serverless edge applications including functions with your own security source code.
- Rules Engine for Edge Firewall: allows you to configure scenarios where specific policies are enforced, providing granular control over delivery.
- Azion Marketplace and Custom Integrations:
- Bot protection.
- Cardstream: card fraud monitoring and prevention by Axur.
- Leakstream: credential leak monitoring by Axur.
- IP Address Reputation: real-time malicious user detection by IPQualityScore.
- Email Validation: email fraud detection by IPQualityScore.
- Phone Validation: phone number verification by IPQualityScore.
- URL Validation: malicious URL detection by IPQualityScore.
- Face Detection: facial biometric verification by Saffe.
- Id Matching: identity verification by Saffe.
- Liveness Detection: anti-spoofing protection by Saffe.
- Observe suite: monitor and track traffic through Real-Time Metrics, Real-Time Events, and Data Stream.
Implementation
- Create an edge application and deploy it to the edge.
- Configure your custom integrations with Azion’s platform.
- Configure the application, including main settings such as origins, cache settings, etc.
- Configure a custom domain for your application.
- Set the criteria and behaviors for the Rules Engine rules. For example:
- Inspect HTTP headers.
- Add or filter cookies.
- Validate input parameters.
- Block malicious payloads.
- Redirects.
- Rewrite the request.
- Set the criteria and behaviors for the Rules Engine rules. For example:
- Deny or drop requests.
- Block malicious IPs.
- Filter specific HTTP requests.
- Enforce rate limits.
- Run edge functions with custom logic.
- Instantiate edge functions and integrations.
- Contact the Sales team for more details on the Bot Manager subscription.
- Monitor your application and refine rules.
Related docs
- Enhance Cybersecurity with Azion’s Advanced WAAP Solution
- Protect Your Edge Applications with a Bot Management Solution
- Secure an application
- Secure an infrastructure
- Secure a DNS
- Implement a security perimeter around your API Gateway
- Accelerate security modernization with edge computing
- Simplify your journey and protect your business with Security Automation
- Strengthen Governance, Risk, and Compliance in Your Organization