Accelerate security modernization with edge computing
Edge computing capabilities can help you safeguard your applications and their content, benefiting you from modern logic that requires minimum management and observability products to monitor requests while focusing on your core business objectives.
By implementing efficient and effective security measures at the edge, you can ensure faster threat detection and response times, leading to a more robust and proactive security posture, as well as significantly reducing latency, enhancing data privacy, and improving overall system resilience.
This use case is ideal for organizations looking to build a strong online presence and protect valuable business assets.
Security Modernization Architecture Diagram
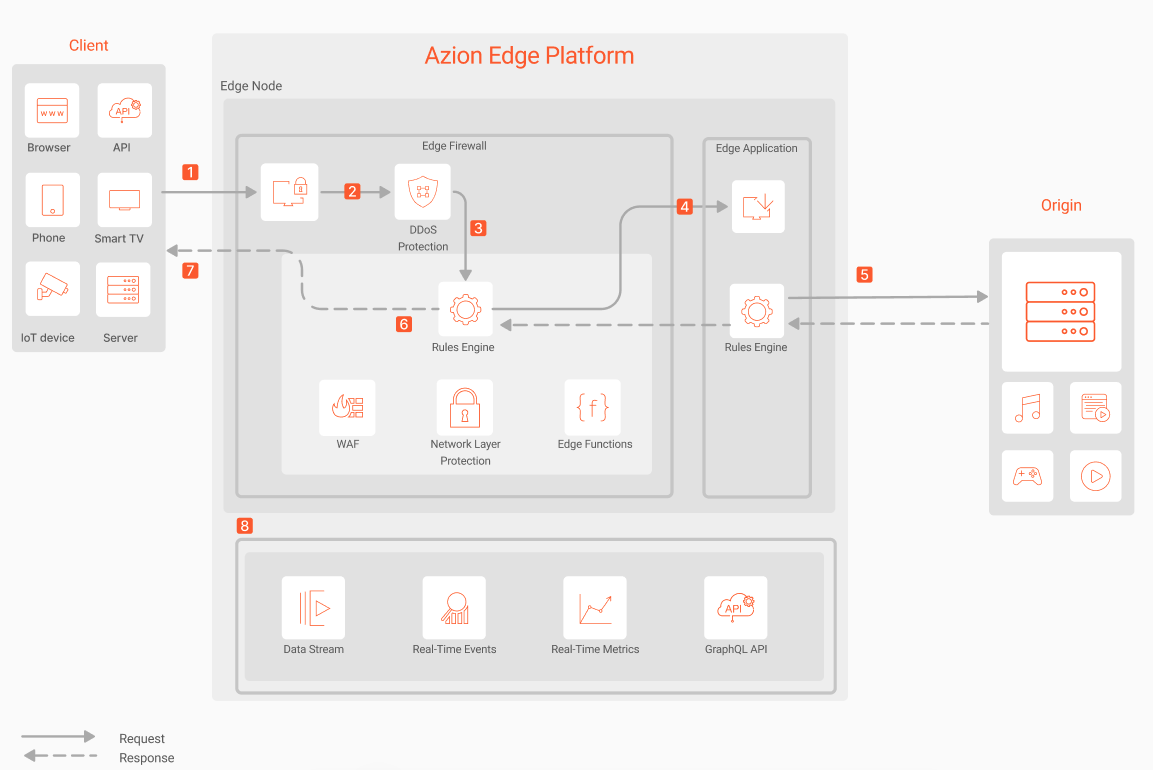
- A request reaches Azion Edge Platform.
- Edge Firewall processes the request.
- DDoS Protection detects if there are DDoS or DoS attacks and either blocks the request and mitigates the attacks or allows the request.
- Edge Firewall Rules Engine identifies if there are rules from WAF, Network Layer Protection, and Bot Manager.
- Edge Application Rules Engine identifies if there are rules related to caching, image optimization, cookies, and redirects, among others.
- If the request doesn’t match an Edge Firewall rule and isn’t blocked, the request continues the flow.
- If the content isn’t cached on the application, the request proceeds to the origin to be processed.
- Edge Application or Edge Firewall Rules Engine executes any rule configured for the Response Phase.
- The final response is delivered to the client.
- Activity can be observed through Real-Time Events, Real-Time Metrics, and GraphQL API or using a Data Stream connector to feed event logs into your stream processing, SIEM, and big data platforms.
Components
- Edge Application: your application running on top of the Azion Edge Platform.
- Edge Firewall: executes its modules and security rules.
- DDoS Protection: detects and mitigates DDoS and DoS attacks.
- Web Application Firewall: allows you to configure protection against attacks and vulnerabilities.
- Network Layer Protection: allows you to create lists with IP addresses or countries with suspicious behavior and restrict their access.
- Edge Functions: serverless functions that run on Azion Runtime with low latency, bringing the operational power and security processing closer to the end user.
- Rules Engine: allows you to create customized security logic through rules to block or allow requests and users.
- Origin Shield: creates a security perimeter for your origin infrastructure.
- Data Stream, Real-Time Metrics, Real-Time Events, and GraphQL API: enable you to monitor all Edge Firewall and modules activity.
Implementation
- Create an edge application using one of the recommended options:
-
Dynamic and Static File Optimization template. To easily deploy this template at the edge, click the button below:
Deploy the Dynamic and Static File Optimization Template
- Create an edge firewall and associate it with the configured domain, so all security rules apply to that specific domain.
- Enable the Web Application Firewall, Network Layer Protection, and Edge Functions modules.
- Create a WAF rule set, configuring Threat Type and Sensitivity levels.
- Create a network list in Network Layer Protection.
- Create your security edge functions or explore marketplace security integrations like reCaptcha, hCaptcha, Secure Token, JWT, and much more.
- Create rules in Rules Engine for Edge Firewall to define the behavior to be executed when the Edge Firewall detects a request matching the criteria defined by the rule sets, network lists, and edge functions.
- Use Observe products to monitor your requests and traffic.
Related docs
- Secure Overview
- Configure Edge DNS main settings
- Web Application and API Protection (WAAP) architecture