Enhance Cybersecurity with Azion's Advanced WAAP Solution
Azion’s Web Application and API Protection (WAAP) ensures robust defense mechanisms against cyber threats such as OWASP Top 10, sophisticated zero-day attacks, and automated bot activities. This architecture guarantees the security and uninterrupted availability of web applications and APIs by employing a comprehensive suite of integrated security features that meticulously analyze and manage incoming requests to protect against a wide range of attacks.
This solution is ideal for organizations looking to safeguard their digital infrastructure against advanced security threats, providing reliable protection for web applications and APIs against the most challenging cyber attacks.
Web Application and API Protection (WAAP) Architecture Diagram
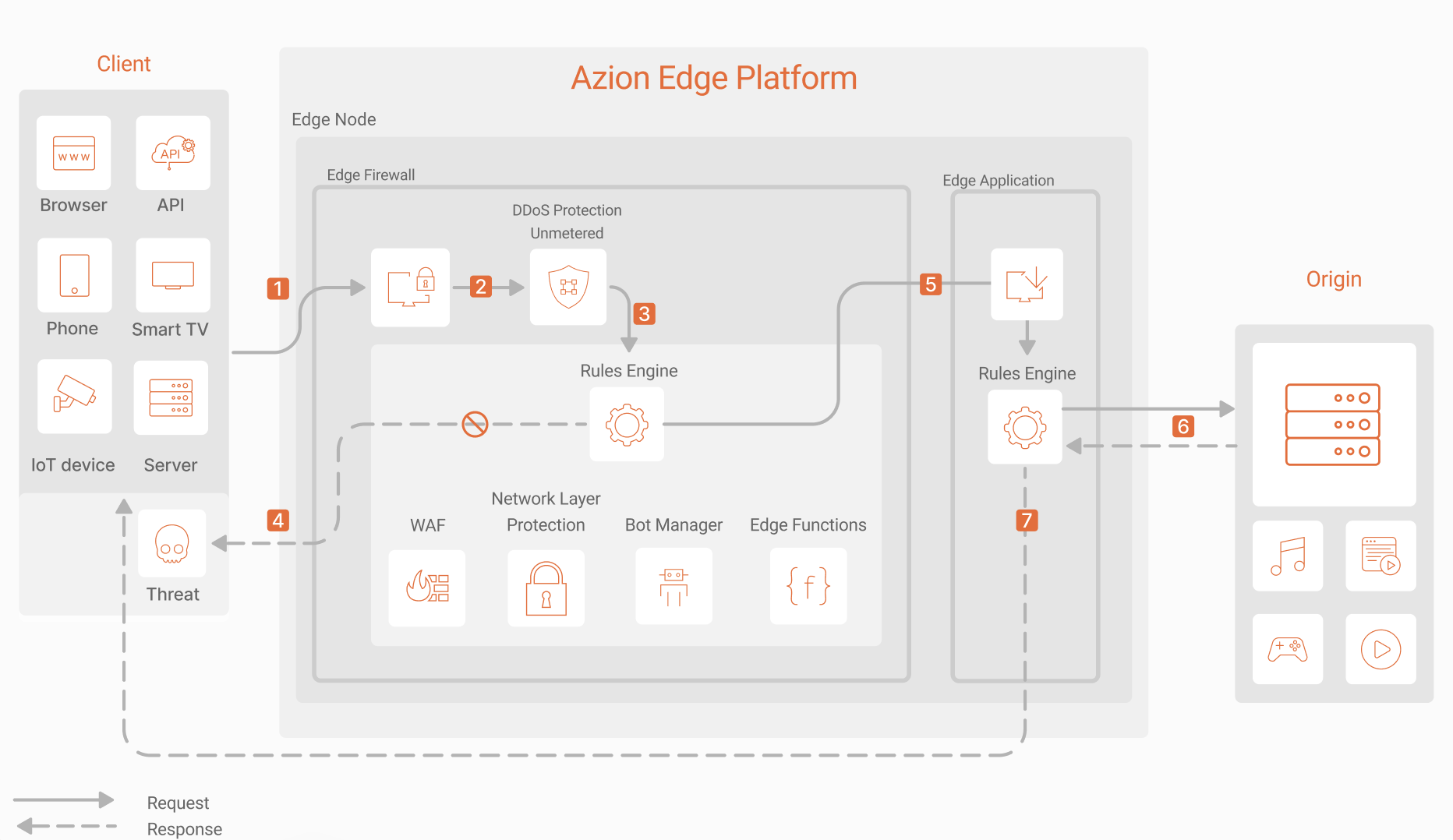
Web Application and API Protection (WAAP) Dataflow
- A request reaches Azion Edge Platform and is redirected to Edge Firewall.
- Edge Firewall processes the request, where DDoS Protection assesses for potential DDoS or DoS attacks, blocking or allowing the request accordingly.
- Edge Firewall’s Rules Engine processes the rules during the request phase; if conditions are met, the corresponding behaviors are executed.
- Rules Engine finalizes execution and sends a response if:
- Network Layer Protection identifies the user or network as a potential threat and applies configured behaviors such as blocking or penalties.
- WAF detects a security threat.
- Bot Manager classifies the device, user, or intent as malicious.
- Security Edge Functions or custom rules, such as rate limiting, deny access or take other preventive actions to protect the application.
- Rules Engine permits the request to proceed to Edge Application.
- Edge Application’s Rules Engine forwards the request to the Origin—whether it be multi-cloud, on-premises, or hybrid—and, upon receiving the response, initiates the Rules Engine’s response phases.
- The client receives the final response.
Components
- Edge Firewall: provides main settings to set up your instance and associate it with domains and activate modules.
- DDoS Protection: detects and mitigates DDoS and DoS attacks when it’s activated.
- Web Application Firewall: allows you to configure protection against attacks and vulnerabilities found in OWASP Top 10 and block requests.
- Network Layer Protection: allows you to create lists with IP addresses or countries with suspicious behavior and restrict their access.
- Bot Manager: identifies and classifies the request according to the intent-based behavioral analysis.
- Edge Application: runs your application on top of the Azion Edge Platform.
Implementation
-
Create an edge application using one of the recommended options:
- Dynamic and Static File Optimization template. To easily deploy this template at the edge, click the button below:
-
Create an edge firewall and associate it with the configured domain, so all security rules apply to that specific domain.
- Enable the DDoS Protection module.
- Enable the Web Application Firewall module.
- Enable the Network Layer Protection module.
-
- Configure Threat Type and Sensitivity levels.
-
Create a network list in Network Layer Protection.
- Configure the IPs or countries that’ll be blocked.
-
- Contact the Sales team for more details on the Bot Manager subscription.
- Configure Bot Manager Lite if you’ve decided to use this version.
-
Create rules in Rules Engine for Edge Firewall.
- Configure the Set WAF Rule Set behavior.
- Configure the Network criteria.
- Configure the Request URI criteria.
Related docs
- Use Azion Observe products to monitor your application delivery, incoming traffic, and how your security logics are being applied and with which requests.