Implement a security perimeter around your API Gateway
API Gateways enable intelligent management and routing of API requests to the appropriate backend microservices across distributed networks. They act as a single entry point for all API requests. While an API Gateway facilitates efficient traffic flow and centralizes control, it also introduces the need for security measures and monitoring to prevent performance issues and security vulnerabilities.
Defining a robust security perimeter ensures that only validated requests pass through, enforcing access control, traffic encryption, and threat detection. With this extra layer of protection, you’re able to prevent unauthorized access, mitigate attacks, and secure sensitive data. This way, your gateway manages traffic and turns into a checkpoint to avoid malicious activity reaching your origins.
Through this perimeter, you can implement solutions such as:
- Rate limiting and throttling to control the volume of API requests.
- Customized WAF rules to address the specific needs of your infrastructure.
- Detection of DDoS attacks, bad bots, and other common threats.
- Authentication mechanisms to secure your edge applications.
- Observability tools to monitor performance and identify threats.
API Gateway Security Architecture Diagram
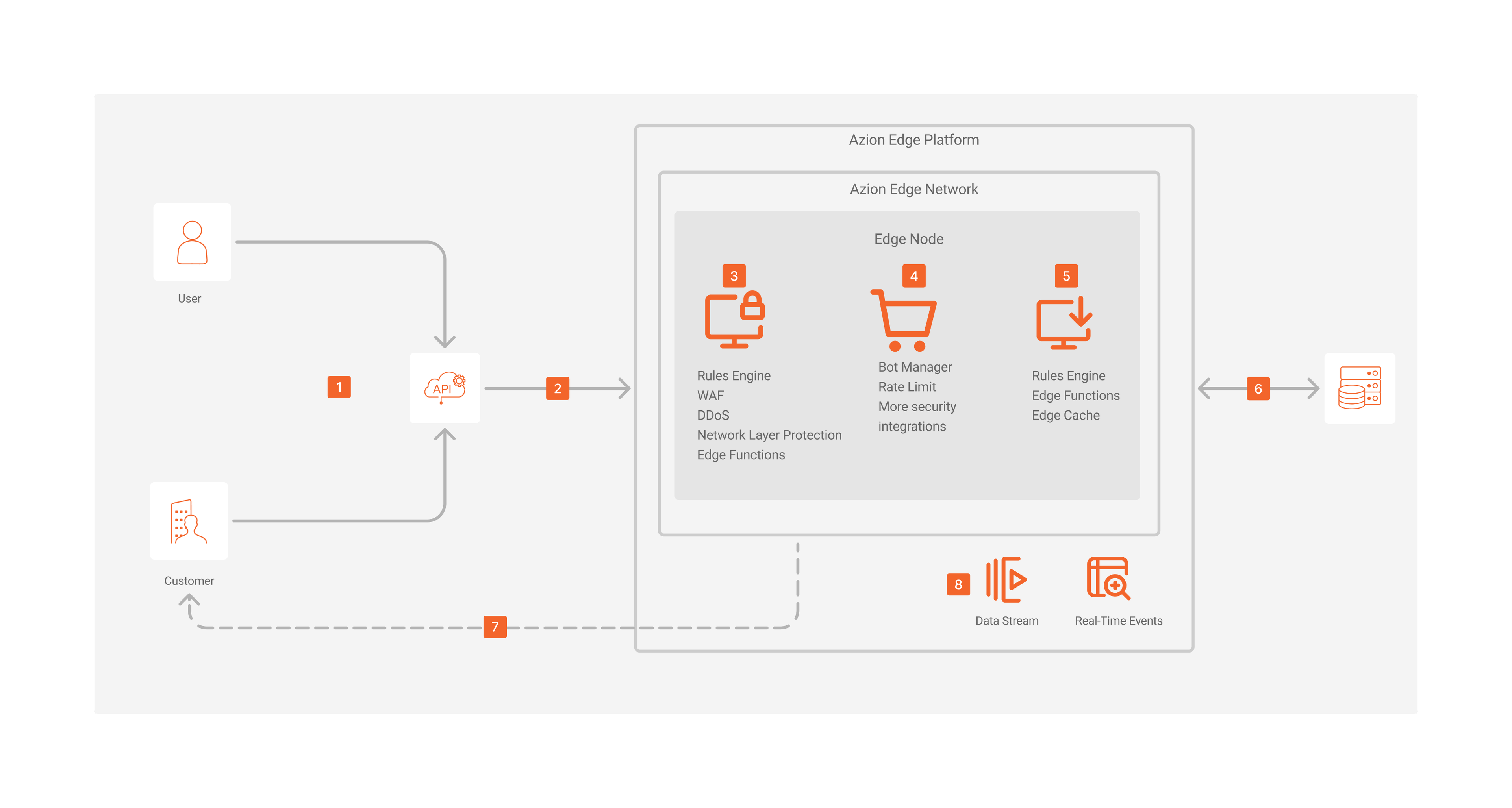
API Gateway Security Dataflow
- A request is sent to the API Gateway.
- In the case of the user, it can be a content request.
- The customer can be a developer using Azion’s platform as an API security perimeter trying to configure and manage policies.
- The API Gateway processes the request and redirects it to the Azion Edge Platform.
- Edge Firewall verifies and analyzes the request to make sure is safe, including Rules Engine Rules, Edge Functions, WAF Rules, DDoS mitigation, network list policies, and more.
- In this step, any authentication account management policy is also applied, such as Multi-Factor Authentication (MFA), account lockout policy, and more.
- Marketplace Integrations for security are executed to complete the analysis and verification.
- Based on the firewall, account management, and integrations’ configurations, the system denies any unauthorized request. Otherwise, the request continues the flow.
- Edge Application verifies and analyzes the request to execute the rules accordingly, such as cache and image optimization.
- The request only reaches the origin in case the edge node doesn’t contain the required response, after passing all the implemented security policies.
- The user receives the response.
- Customers can monitor all the activity through the Observe products.
- SIEMs systems can also be implemented through Data Stream connectors.
Components
- Edge Application: allows you to set up an edge application to configure delivery and cache policies.
- Edge Firewall: provides main settings to set up your instance, enabling you to associate it with domains and activate modules to protect users, applications, and networks.
- Web Application Firewall: allows you to configure protection against attacks and vulnerabilities.
- DDoS Protection: detects and mitigates DDoS and DoS attacks.
- Network Layer Protection: allows you to create lists with IP addresses or countries with suspicious behavior and restrict their access.
- Edge Functions for Edge Firewall: build event-driven, serverless edge applications including functions with your own security source code.
- Marketplace Integrations: edge function-based functionalities to compose and improve your applications, enforcing security policies.
- Data Stream and Real-Time Events enable you to monitor all API Gateway activity.
Implementation
- Implement your API Gateway.
- Create an edge application.
- You can use Azion Console, Azion API, or Azion CLI to create and deploy an edge application.
- Configure the application’s main settings.
- Associate your API Gateway custom domain with the edge application.
- Create your Digital Certificates.
- Create an edge firewall and select the domain you want to protect.
- Define any WAF rules, Rules Engine rules, or edge functions you want to implement and instantiate in the firewall.
- Install and configure the Azion Integrations you want to use to enhance your security policies.
- Monitor your API Gateway behavior through the Observe products.
Related docs
- API security
- Enhance cybersecurity with Azion’s Advanced WAAP Solution
- Protect your edge applications with a Bot Management solution
- Accelerate security modernization with edge computing
- Strengthen Governance, Risk, and Compliance in your organization
Contributors