Strengthen Governance, Risk, and Compliance in Your Organization
Azion helps its customers achieve compliance while ensuring the security and performance of their edge applications. To do so, through advanced strategies and technologies, Azion protects its edge network and platform, continuously updating policies and certifications to meet market standards. With industry validations such as SOC 2 Type II and PCI DSS v4.0 Level 1 Service Provider, Azion offers a compliant platform that simplifies Governance, Risk, and Compliance (GRC) strategies. This allows customers to develop and deploy new applications in a secure, compliant environment, ensuring adherence to both internal and market-required GRC policies.
How Azion helps clients ensure compliance
Azion supports compliance efforts at multiple levels by offering robust security tools, certifications, and a flexible infrastructure.
- Compliant infrastructure: Azion’s platform is fully compliant with PCI DSS v4.0 Level 1 Service Provider and SOC 2 Type II, providing customers with a secure, certified platform that reduces the need to manage compliance from scratch.
- Security configurations and policies: customers can customize security configurations like access control, traffic filtering, and encryption through Azion’s tools, ensuring alignment with specific GRC policies.
- Shared responsibility: compliance is shared, with Azion securing the platform and customers managing application-specific controls like access policies and data encryption.
- Support and incident response: Azion’s Security Response Team (SRT) helps customers manage incidents and monitor security to maintain ongoing compliance.
- Certificate management: Azion enables customers to manage digital certificates, ensuring secure, encrypted communications, particularly for sensitive data transmission.
About Shared Responsibility
For customers to maintain compliance, they must actively engage in configuring and managing security controls within their environments. Some key responsibilities of the customer include managing user access, monitoring and reviewing logs, securing data transmission, configuring security policies specific to their applications, and handling vendor accounts and authentication.
Additionally, customers must be cautious of using default or weak credentials, neglecting regular reviews and audits, disabling security controls, overlooking certificate management, and other practices that could generate compliance breaches and security vulnerabilities.
Governance, Risk, and Compliance Architecture Diagram
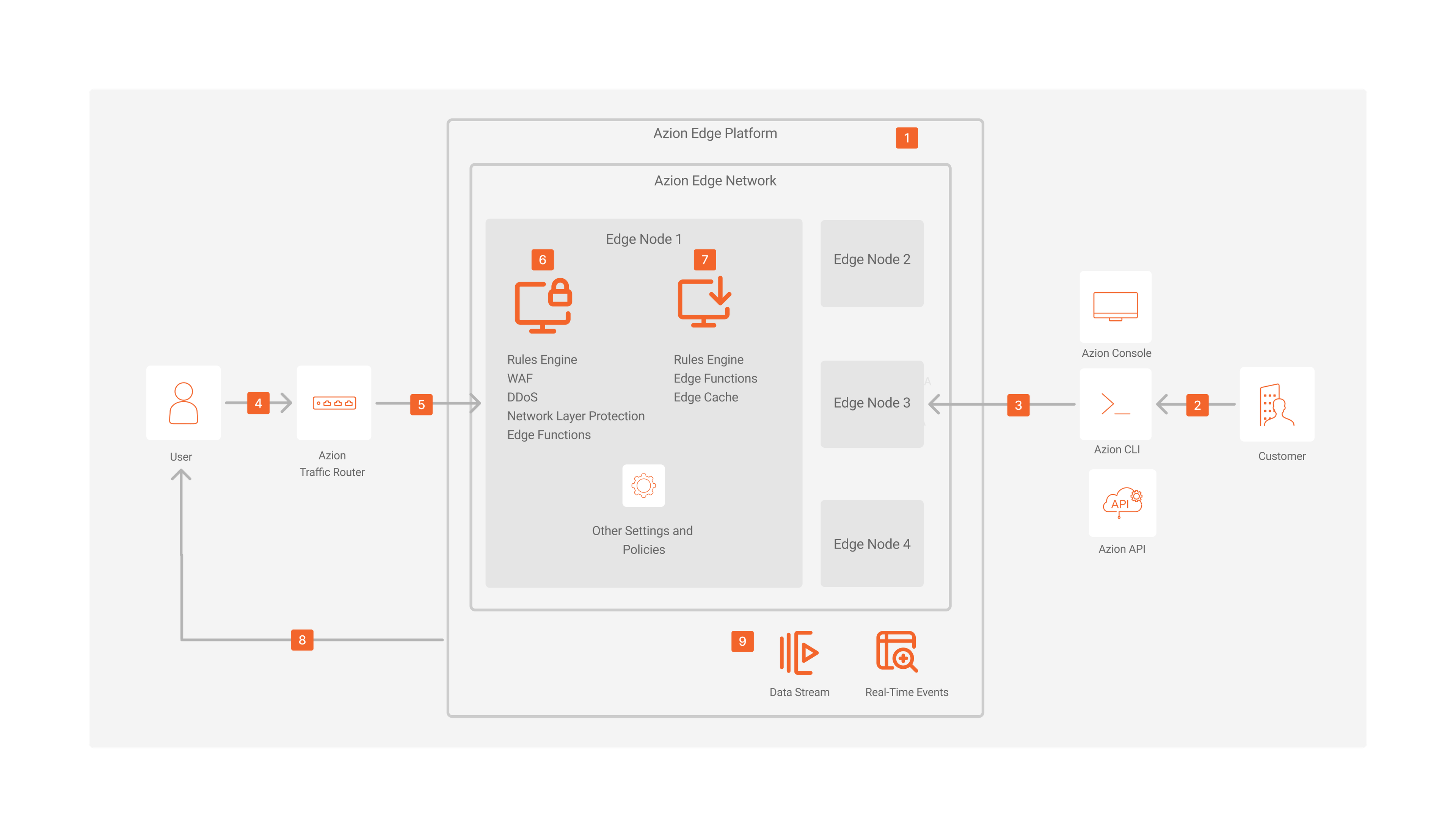
Governance, Risk, and Compliance Dataflow
- Azion team defines global policies and implements certifications to guarantee network and platform security.
- The customer deploys infrastructure and applications on the edge, setting up customized rules and policies to be GRC compliant.
- These rules and policies are replicated across the network, guaranteeing any node is going to execute them when requested.
- A final user sends a request to an application hosted on Azion’s platform.
- Azion Traffic Router identifies the healthiest Edge Node to process the request.
- In the Edge Node, Edge Firewall verifies and analyzes the request to make sure is safe, including Rules Engine Rules, functions, WAF rules, DDoS mitigation, network list policies, and more.
- Based on the configurations, the system denied any unauthorized request. Otherwise, the request continues the flow.
- Edge Application verifies and analyzes the request to execute the rules accordingly, such as cache, and image optimization, among others.
- The user receives the response.
- Customers can monitor all the activity through the Observe products.
Components
- Edge Network: it processes data closer to the source, reducing latency and enhancing real-time analysis, including policies and technologies to make it safe and compliant.
- Azion CLI: an open-source command-line interface (CLI) that lets you interact with Azion Edge Platform using a terminal.
- Azion Console: Azion’s interface where you can access all the available products and their settings.
- Edge Firewall: provides main settings to set up your instance, enabling you to associate it with domains and activate modules to protect users, applications, and networks.
- Web Application Firewall: allows you to configure protection against attacks and vulnerabilities.
- DDoS Protection: detects and mitigates DDoS and DoS attacks.
- Network Layer Protection: allows you to create lists with IP addresses or countries with suspicious behavior and restrict their access.
- Edge Functions for Edge Firewall: build event-driven, serverless edge applications including functions with your own security source code.
- Edge Application: allows you to set up an edge application to configure delivery and cache policies.
- Real-Time Events enables you to monitor all your applications’ activity and by using Data Stream connectors you can feed event logs into your stream processing, SIEM, and big data platforms.
Implementation
- Add user, define team permissions, and set up account policies, such as Single Sign-On (SSO), Multi-Factor Authentication (MFA), or User Session Timeout.
- Create an edge application.
- You can use Azion Console, Azion API, or Azion CLI to create and deploy an edge application.
- Configure the application’s main settings.
- Create a domain and associate it with the edge application, and point your traffic to Azion.
- Create your Digital Certificates.
- Create an edge firewall and select the domains you want to protect.
- Define any WAF rules, Rules Engine rules, or edge functions you want to implement and instantiate in the firewall.
- Monitor your applications through the Observe products and the Activity History page.
Related docs
- Azion certifications and compliance
- SOC Compliance
- PCI Compliance
- Azion Security Response Team (SRT)